Water and wastewater systems have become targets for cyberattacks, according to a joint advisory released by the EPA, FBI, Cybersecurity and Infrastructure Security Agency (CISA), and National Security Agency (NSA). These attacks are expected to continue or increase in the United States and globally.

Jump to…
Learn
Recommended Actions
Reporting a Cyber Attack
Free Assistance
Funding
Current Threat Assessments
Learn about Cybersecurity
Cybersecurity means taking action to guard your computer systems and data against unauthorized access that could result in theft, damage, or disruption of service. Potential damage caused by a cyberattack to a water or wastewater system includes lost productivity, operational disruption, the cost of ransom, the cost of repairing or installing new computer systems, theft of customer data, danger to public health or the environment, and loss of customer confidence.
The types of cyberattacks that pose the greatest threat to water and wastewater systems are ransomware, phishing, and outdated software/technology.
Ransomware is a malicious software (or “malware”) that is designed to block you from using your computer system or accessing your data until a ransom is paid. This could potentially shut down operations at your system. A computer can become infected with ransomware if you click a malicious internet link or email attachment. The criminal gains access to your computer system, blocks you from using it, and often asks for a large ransom payment. Watch a video about ransomware.
Phishing is an attempt to gain remote access, sensitive information, or payment through a fake email that is designed to look real. The email poses as a familiar person or company to try to get you to send personal information, passwords, or money, or trick you into clicking a malicious link or attachment that contains ransomware. (Phishing can also take the form of a phone call or text message.) If an employee falls victim to a phishing attack, the whole system is at risk of a cyberattack—so be sure all personnel are trained in cybersecurity. Watch a video about phishing.
Outdated software/technology are easy targets for hackers because the security may no longer be supported or effective. Hackers may be able to gain access to your system this way and block you from using your computers or steal your data. Keep your software up-to-date and use strong passwords and multifactor authentication.
There are also unintentional cyber incidents, such as if a fiber to your building is accidentally cut, leaving the utility without internet connection for an extended time.
More Educational Resources
Water Sector Cybersecurity Guide from EPA
EPA’s Cybersecurity Checklist (questions start on page 19, fact sheet starts on page 25)
Top Cyber Actions for Securing Water Ssytems from EPA, CISA, and FBI
Recommended Actions
Here are some steps you can take on your own to protect your facilities. For the more complicated aspects of cybersecurity, we encourage you to contact CISA or EPA for free assistance (see next section).
For All Personnel:
-
- Learn to identify malicious emails, ransomware, and phishing
- Use strong passwords and multi-factor authentication
- Keep computers and other devices updated to the latest version
- Report suspicious activity of any kind to the Vermont Intelligence Center at 844-848-8477 or the anonymous online tip line
- If your system is under attack, call Vermont Emergency Management at 800-347-0488
For Managers:
-
- Create an inventory of devices and the people who have access to them
- Ensure your facility’s physical security prevents unauthorized access to devices
- Include cybersecurity best practices in your Operations & Maintenance (O&M) Manual
- Train all staff on cybersecurity best practices
- Include cyber attacks in your Emergency Response Plan, and practice responding to a cyber incident
- Use EPA’s Cybersecurity Checklist (questions start on page 19, fact sheet starts on page 25) to assess your system’s cybersecurity
- Ensure security protocols and routine updates are included in contracts with IT consultants and/or SCADA providers
- Have a third-party cybersecurity risk assessment performed (see below for free options)
- Enroll in free vulnerability scanning for water utilities (see below)
- Read CISA’s Cybersecurity Incident Response Guide
For IT/SCADA Technicians:
-
- Keep devices and software programs updated to the latest version
- Create an inventory of devices, software, networks, and the people who have access to them
- Back up critical data
- Use network firewalls
- Restrict remote connections to SCADA systems
- Turn off remote access software when not in use
In the Event of a Cyber Attack
If your system is experiencing a cyber attack, you should call Vermont Emergency Management at 800-347-0488. VEM will help coordinate the emergency response, including assistance from the FBI or Cybersecurity and Infrastructure Security Agency (CISA) if needed.
You must report any non-routine operating procedures or public health risks to the appropriate regulatory agency. For drinking water, call Matt Hunt at 802-505-5490. For wastewater, call Amy Polaczyk at 802-490-6185.
If the cyber attack impacts your SCADA system or PLCs, contact the service provider. If you have IT staff or a consultant, contact them.
If you need extra workers or equipment, reach out to the VT WARN mutual aid network at dec.vermont.gov/vtwarn
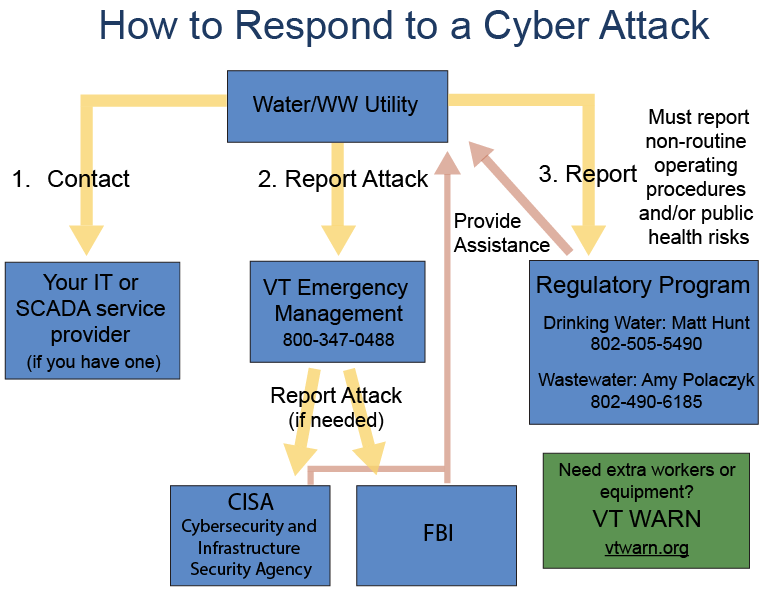
Learn more about emergency response during a cyber attack in CISA’s Water and Wastewater Sector Incident Response Guide. For federal reporting options, see this flyer from EPA.
Free Assistance & Resources
1. The Cybersecurity and Infrastructure Security Agency (CISA) is a branch of the Department of Homeland Security that assists the nation’s critical infrastructure with physical security and cybersecurity. See www.cisa.gov/water
-
- CISA can perform an assessment of your system and advise you on steps you can take to improve your physical and cyber security. These services are free, voluntary, and non-regulatory. The assessment generally takes place in-person at your facility. Find more information at www.cisa.gov/how-we-can-help-region-resources and email CISAregion1@hq.dhs.gov to request services.
- CISA has a free vulnerability scanning service for water and wastewater systems. It can automatically scan your system for cybersecurity vulnerabilities and send you a weekly report. See the fact sheet for more information. To enroll, email vulnerability@cisa.dhs.gov with the subject line “Requesting Vulnerability Scanning Services.”
2. The EPA has launched a Water Sector Cybersecurity Evaluation Program to provide free cybersecurity assessments. The assessment happens virtually and takes about 45–90 minutes. They can also help you develop a cyber action plan. Learn about the program here and sign up for an assessment here.
3. The cybersecurity company Dragos offers their products to water utilities for free through the Community Defense Program. This includes software that provides asset inventory, threat detection, and vulnerability management, as well as access to training resources. Learn more and sign up at www.dragos.com/community-defense-program
Funding
The State Homeland Security Program (SHSP) from Vermont Homeland Security provides grants to federal, state, local, and private sector entities for physical security and cybersecurity. Applications are due in February of each year. See https://hsu.vermont.gov/homeland-security-unit/funding-opportunities/SHSP
The Catalyst Program from the Northern Border Regional Commission (NBRC) is a grant program for local governments and nonprofits. Funding can be used to “revitalize and modernize essential infrastructure.” See https://www.nbrc.gov/content/Catalyst
The State of Vermont has State Revolving Funds (SRF) for water and wastewater. Physical security and cybersecurity are eligible projects. Be aware that these are loans, not grants. Project priority list applications are due each year in January.
Drinking Water State Revolving Fund: https://dec.vermont.gov/water-investment/water-financing/dwsrf
Clean Water State Revolving Fund: https://dec.vermont.gov/water-investment/water-financing/cwsrf
Current Threat Assessments and Vulnerability Issues
11/27/23 A water system in Pennsylvania experienced a cyber attack over the weekend. Attackers were able to gain control of a remote booster station by attacking a programmable logic controller (PLC) made by the company Unitronics. Water and wastewater systems are advised to do the following:
- Check if if any Unitronics PLCs are used at your system.
- Check for signs the PLC has been compromised. This may be a red background saying the unit has been hacked.
- If the PLC may have been compromised, take the device offline and switch to manual operations
- Confirm you are not using the Unitronics PLC default password of “1111”
Read more about this attack from WaterISAC
Read more from CISA
3/21/22 The Biden Administration announced that evolving intelligence indicates that the Russian government is exploring options for potential cyberattacks against the US. This is believed to be is a retaliation against economic sanctions imposed on Russia by the US and its allies in response to Russia’s invasion of Ukraine. Read the statement.
2/23/22 The current situation in Russia and Ukraine has the FBI and CISA warning of Russian state-sponsored cyber attacks on US critical infrastructure, including water and wastewater systems. Russia has a history of both low-sophistication attacks (such as fake emails and guessing password) and high-sophistication attacks, like targeting operational technology (OT) and industrial control systems (ICS) networks with destructive malware. Read more here.
2/9/22 Due to the globalized threat of ransomware, the US, Australia, and the United Kingdom released a joint advisory strongly encouraging every executive and leader to ensure their organization is taking appropriate action to reduce their risk of ransomware. Stopransomware.gov has resources on reducing risk to ransomware or responding to a ransomware attack. Read the Advisory.
11/22/21 The FBI and CISA remind organizations to continue cybersecurity best practices during the holiday season, citing a report that many of the most disruptive ransomware attacks in 2021 have occurred over holidays and weekends. Read the notice.
10/14/21 EPA, the FBI, the Cybersecurity and Infrastructure Security Agency (CISA), and the National Security Agency (NSA) released a joint advisory warning of “ongoing malicious cyber activity…targeting the information technology (IT) and operational technology (OT) networks, systems, and devices of water and wastewater systems”. Read the advisory.
5/20/21 US Department of Homeland Security (DHS) Office of Intelligence released an assessment stating that cyberattacks against water and wastewater systems are expected to increase in the United States and globally. The assessment said that cyber criminals may have the goal of receiving ransom payment or may be targeting the water sector in the context of a social/political conflict or ideological cause. Read the analysis.
5/14/21 Secretary of Homeland Security issued a bulletin on the heightened threat of domestic terrorism in the United States. It does not mention threats specific to water or wastewater systems, but it is still a good idea to review your utility’s physical security and Emergency Response Plan. The bulletin is in effect through August 13, 2021. Read the bulletin.
Last updated 12/1/23

